CloudFormation Git Sync: Automating Infrastructure as Code
CloudFormation Git sync has gotten complicated with all the GitHub Actions workflows, AWS credentials management, and deployment pipelines flying around. As someone who’s automated infrastructure deployments across multiple AWS accounts for the past several years, I learned everything there is to know about keeping CloudFormation templates in version control and automatically deploying them. Today, I will share it all with you.
AWS CloudFormation is a cornerstone of infrastructure as code (IaC) on AWS. It allows you to model and set up your entire AWS infrastructure using a template file. A key feature of IaC is version control, which is where Git comes in. Combining CloudFormation with Git streamlines development processes. This integration provides consistency, accountability, and efficiency in managing cloud resources.
Understanding CloudFormation Templates
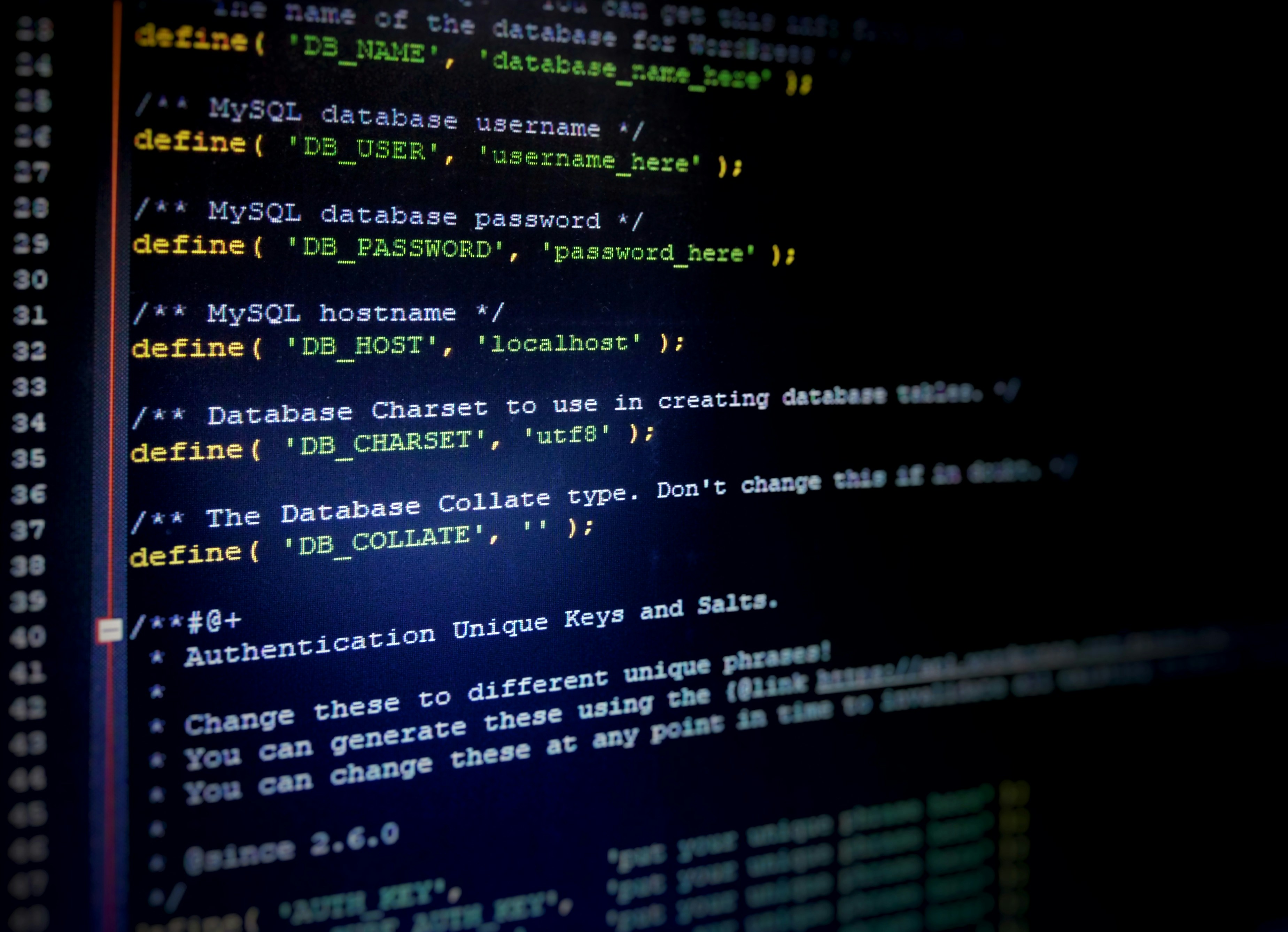
CloudFormation templates are JSON or YAML formatted text files. They describe the AWS resources you want to provision. The template serves as the single source of truth for your infrastructure. It supports various resources such as EC2 instances, S3 buckets, and VPCs, to name a few. You define the configuration, and CloudFormation takes care of provisioning and configuring.
Probably should have led with this section, honestly—understanding template structure is fundamental before you start automating deployments.
Within the template, you specify the infrastructure’s components, dependencies, and runtime parameters. This declarative approach ensures that AWS knows exactly what and how to create resources. Parameters, mappings, resources, and outputs are some key sections of a template. Parameters allow you to customize variables for different environments. Mappings can help you organize data values in a template better. Outputs provide means to export resource details for cross-stack references—I use outputs constantly to pass VPC IDs or security group IDs between stacks.
Integrating Git for Version Control
Git is a distributed version control system. It tracks changes and supports collaborative code development. By storing your CloudFormation templates in a Git repository, you gain version control benefits. These include maintaining a history of changes, easily reviewing who made modifications and when, and the ability to roll back to previous versions.
That’s what makes Git integration endearing to us cloud engineers—no more “which version of the template is actually deployed right now?” questions. The Git history tells you exactly what changed and when.
Using Git with CloudFormation encourages collaboration among team members. It enables structured development workflows through branching and pull requests. Branching lets you work on feature or bug fixes in isolation. Pull requests provide opportunities for code review and effective team communication. When coupled with CloudFormation templates, it brings a robust means of managing infrastructure evolution. I’ve caught countless typos and misconfigurations during PR reviews that would have caused production outages.
Setting Up GitHub Actions for Continuous Deployment
GitHub Actions can automate workflows for continuous deployment of CloudFormation stacks. By defining a workflow in a YAML file, you configure triggers for actions, such as pushes to a repository. A simple setup involves specifying triggers, defining jobs that encapsulate actions, and detailing the steps for each job. For infrastructure deployment, you can use AWS CLI commands within these steps.
Begin by creating a new YAML file in the .github/workflows directory of the repository. Define the workflow to trigger on pushes to a specific branch, like main. Then specify a job that runs on a particular environment, for example, ubuntu-latest. You can define pipeline steps such as setting up AWS credentials, validating the CloudFormation template, and executing stack updates or creation. The first time you see your infrastructure automatically deploy after a git push, it feels like magic.
Connecting AWS and GitHub with Secrets
For GitHub Actions to interact with AWS, you need to authenticate. GitHub secrets provide a secure way to store sensitive information such as AWS Access Keys. Using the GitHub web interface, navigate to your repository settings. Under the secrets section, add the necessary AWS keys typically named AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY.
Better yet, use OIDC (OpenID Connect) with AWS IAM roles instead of long-lived access keys. This avoids storing credentials entirely and follows AWS security best practices. I migrated all my workflows to OIDC after one too many security audits flagging static credentials.
Reference these secrets within the GitHub Action YAML using contexts and expressions. Within the steps of your action, set environment variables or pass the secrets directly into AWS CLI commands. This connection ensures that GitHub Actions have the required permissions to deploy CloudFormation stacks, staying secure and efficient.
Implementing a Basic CloudFormation Sync Workflow
Let’s look at a basic GitHub Actions workflow for CloudFormation. Start by defining the workflow file deploy.yml placed in the .github/workflows folder. Configure it to trigger on push events to the main branch. Within the jobs section, use Ubuntu as the runner image.
- First, check out the repository using the
actions/checkoutaction. - Next, configure the AWS environment by exporting the keys from GitHub secrets.
- Validate the CloudFormation template using AWS CLI. Syntax like
aws cloudformation validate-template --template-body file://template.yamlensures errors are caught early. Trust me, you want this step—finding a syntax error after deployment starts is painful. - Deploy or update the CloudFormation stack. Use the
aws cloudformation deploycommand, including necessary parameters such as stack-name and the template file path. - Optionally, add additional steps to notify stakeholders or run tests. I always add a Slack notification step so the team knows when deployments complete.
This pipeline automates the process and reduces manual intervention. It enhances the reliability of infrastructure changes and brings transparency. Committing code updates directly initializes infrastructure provisioning, aligning with DevOps principles.
Best Practices for CloudFormation Git Sync
Consider adopting the following best practices to optimize your CloudFormation-Git integration. Validate templates locally before committing changes. This minimizes the introduction of errors into the main branch. Maintain a branching strategy that supports your team’s workflow. Feature branches, pull requests, and regular merges promote a healthy codebase.
I use tools like cfn-lint and cfn-nag locally to catch issues before they hit CI/CD. These tools have saved me from embarrassing mistakes more times than I can count.
Enforce quality checks through code reviews. Reviewing CloudFormation templates before deployment helps identify potential issues early. Integrate logging and monitoring within your CloudFormation settings. Using AWS services such as CloudWatch grants visibility into deployed resources’ performance and changes.
Regularly back up your CloudFormation state with automated scripts. This ensures recovery from errant stack updates is prompt and stress-free. Use stack policies to protect parts of your stack from accidental updates or deletions. This safeguard adds an extra layer of security to crucial infrastructure components—I learned this the hard way after accidentally deleting a production database.
Enhancing Security within CloudFormation Deployments
Security remains a top concern in cloud infrastructure management. Employ AWS Identity and Access Management (IAM) roles judiciously within your CloudFormation templates. Assign the least privilege necessary to perform stack actions. This minimizes potential vulnerabilities and access to sensitive features.
Integrating AWS Config or Config Rules with CloudFormation ensures compliance. Configure your stacks to adhere to organizational standards and policies. Automated checks through AWS Config ascertain that resources remain secure and compliant throughout their lifecycle. These compliance checks catch drift before it becomes a problem.
Apply encryption wherever applicable. For instance, enable encryption at rest for data services such as RDS or S3 via your CloudFormation configurations. Utilize AWS Key Management Service (KMS) to manage encryption keys and policies. By embedding these security features in your templates, you fortify the entire infrastructure stack from the ground up.
Leveraging Advanced Features in CloudFormation
CloudFormation provides several advanced features to further enhance IaC deployments. Use change sets to preview the impact of a stack update without implementing changes. This allows detailed review and preemptive correction of resource modifications before executing updates. Change sets are mandatory in my workflow—I never deploy to production without reviewing the change set first.
Stack sets enable cross-region or multi-account deployments. This feature aids in managing global infrastructure from a central point, improving efficiency and uniformity. Nested stacks help organize large templates by dividing resources across smaller, reusable chunks. This modularization simplifies complex infrastructure patterns and promotes template reuse.
Utilizing the AWS Cloud Development Kit (CDK) can streamline the creation of CloudFormation templates programmatically. CDK enables defining cloud resources using programming languages like TypeScript or Python, appealing to developers who prefer coding over static templates. I’ve moved most of my new infrastructure to CDK—being able to use loops and conditionals makes template generation so much easier.
Ensuring High Availability and Reliability
Design your CloudFormation stacks with redundancy and failover capabilities. Distribute resources across multiple availability zones within a region. Use Elastic Load Balancers and Auto Scaling to maintain application uptime and performance. Define target tracking policies within templates to automate scaling based on resource load.
That’s what makes CloudFormation endearing to us cloud engineers—it codifies resilience patterns that would otherwise require manual configuration across dozens of resources.
Embrace continuous integration and continuous deployment (CI/CD) practices. Regular stack updates, testing, and redundancy checks ensure system resilience. Automate failure detection and recovery processes via CloudFormation configurations. Incorporate mechanisms such as RDS Multi-AZ deployments to withstand regional outages.
Back-up and replication strategies should be embedded in your infrastructure. Utilize S3 replication or cross-region backups to secure critical data assets. By integrating these concepts into your CloudFormation templates, you enhance the durability and availability of cloud resources, minimizing downtime and disruption costs.
Managing CloudFormation Costs with Git Sync
Effective cost management is achievable through strategic CloudFormation and Git sync setups. Regularly review and optimize your stack configurations to minimize unnecessary expenditures. Use AWS Cost Explorer to monitor usage patterns and adjust resources accordingly.
Tagging resources promotes tracking and accountability. Define tags within your CloudFormation templates to reflect the purpose, owner, and environment of the resources. Tags assist in visibility for chargeback, budget allocation, and compliance reporting. Consistent tagging is non-negotiable in multi-team environments.
Implement scheduling for resources such as EC2 instances to operate during peak business hours only. Use Lambda functions integrated through CloudFormation to start or stop instances based on predefined schedules. Such automation aligns infrastructure usage with business demand, reducing operational costs. I’ve seen organizations cut EC2 costs by 40% just by shutting down dev environments overnight.
Explore spot instances or reserved instances where applicable, and configure them within your CloudFormation templates. These options provide cost-effective alternatives to regular on-demand resources. Monitor and audit your templates frequently to identify potential cost savings. Incorporate them directly into the operational pipeline via Git commits and CloudFormation updates.
Troubleshooting Common CloudFormation Git Sync Issues
Even with solid automation, things go wrong. Stack updates fail, change sets show unexpected resource replacements, or GitHub Actions workflows timeout. Knowing how to debug these issues quickly is critical.
When a stack update fails, check CloudWatch Logs for detailed error messages. CloudFormation events provide a chronological view of what resources were being modified when the failure occurred. Common issues include insufficient IAM permissions, resource naming conflicts, or dependency ordering problems. I keep a runbook of common error codes and their solutions—it saves hours of troubleshooting.
GitHub Actions failures often stem from credential issues or timeout settings that are too aggressive. Enable debug logging in your workflow with ACTIONS_STEP_DEBUG to see detailed output. Check that your IAM policies grant the necessary CloudFormation permissions—not just cloudformation:*, but also permissions to create and modify the underlying resources.
Real-World Implementation Tips
Start small when implementing CloudFormation Git sync. Don’t try to migrate your entire infrastructure at once. Begin with a non-critical development environment to validate your workflow. Test the full cycle: make a template change, commit to Git, watch it deploy automatically, then verify the infrastructure matches your expectations.
Document your deployment process thoroughly. Create a README in your repository explaining the directory structure, naming conventions, and deployment workflow. Include examples of how to add new stacks and how to handle rollbacks. Future you (and your teammates) will appreciate it.
Establish clear conventions for your team. Decide on naming patterns for stacks, parameter files, and Git branches. Use consistent tagging across all resources. Create template for common infrastructure patterns so new team members can quickly spin up standardized environments. The time invested in standardization pays dividends in reduced confusion and faster onboarding.
The Future of Infrastructure as Code
CloudFormation Git sync represents where infrastructure management is heading. The lines between application code and infrastructure code continue to blur. Tools like AWS CDK, Terraform, and Pulumi are pushing IaC towards actual programming rather than configuration files. But the core principles—version control, automated deployment, code review—remain constant.
Integration with AI and machine learning will likely enhance IaC workflows in the future. Imagine systems that automatically optimize your infrastructure configurations for cost and performance, or that predict and prevent deployment failures before they occur. We’re already seeing early versions of this with AWS services like Compute Optimizer and Cost Anomaly Detection.
Policy-as-code and compliance-as-code will become standard practice. Instead of documenting compliance requirements in spreadsheets, teams will encode them directly into deployment pipelines. AWS Config Rules, Service Control Policies, and CloudFormation Guard are already moving in this direction. The infrastructure that doesn’t meet compliance requirements simply won’t deploy.



Stay in the loop
Get the latest wildlife research and conservation news delivered to your inbox.